We will be attending DerbyCon which means shipments will be slightly delayed. Any orders from 9/18 to 10/2 will be processed on 10/3 when we are back in office. Thanks for staying patient and being supportive of us while we are out on travel.
The team will be out in Las Vegas for summer camp – Black Hat USA, Bsides LV, and DEF CON. This means orders from 7/18 to 7/31 will go out starting 8/1. Shipments might be delayed further if inventory gets sold out at the conferences. If you are out there, stop by our booth and say hello. We will also have several contests and guest appearances.
We will be attending DerbyCon this coming week/weekend which means shipments will be slightly delayed. Any orders from 9/19 to 9/26 will be processed on 9/27 when we are back from Kentucky.
The team will be out in Las Vegas for summer camp – Black Hat USA, Bsides LV, and DEF CON. This means orders from 7/27 to 8/9 will go out starting 8/10. Shipments might be delayed further if inventory gets sold out at the conferences. If you are out there, stop by our booth and say hello!
Last year Garrett supported a new TV show called ‘Sense8’ which is a Netflix original. He provided them some hacking equipment and provided input into hacking scenes. That series was released a few months ago and here are some screens with the hacking equipment he provided.


A simpleWiFi 8dbi directional antenna close up shot!

Ubertooth One, IronKey encrypted storage device, and Datalocker encrypted storage device.
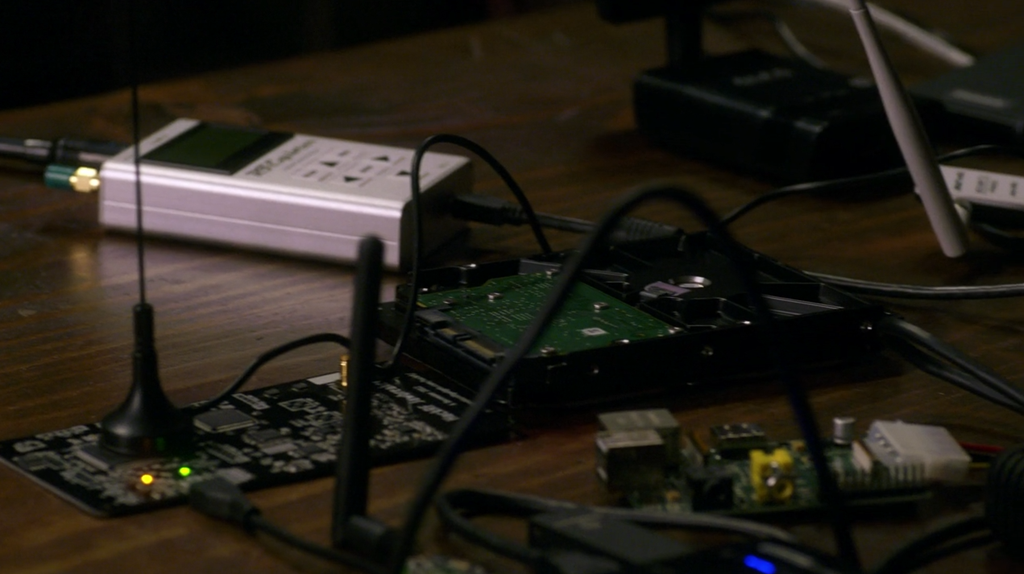
RF explorer, HackRF Jawbreaker, raspberryPi
The dust has settled a bit from all the DEF CON fun and I can now highlight the new products that we brought to DEF CON but haven’t put them on the website until today.
Portable Personal Firewall

A super small dual 10/100 ethernet device that runs linux with iptables/NAT enabled by default and runs off usb power. Perfect for when you need to separate your computer and the network.
ChipWhisperer-Lite
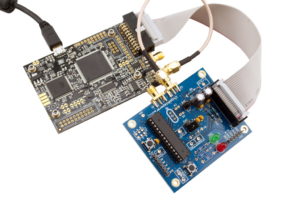
An open source embedded hardware security research tool that has side-channel power analysis and glitching capabilities.
The Hacker Playbook 2

This second version of The Hacker Playbook takes all the best “plays” from the original book and incorporates the latest attacks, tools, and lessons learned. Double the content compared to its predecessor, this guide further outlines building a lab, walks through test cases for attacks, and provides more customized code.
Blinky Grid and Blinky POV

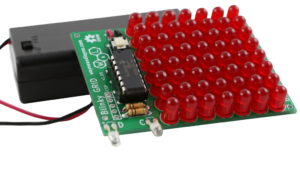

Two kits to practice your soldering skills. Both are message displays through LEDs.

This year’s DEF CON was fun as usual. Exhausting, but quite fun. I hope those that caught the Con-Flu have a quick and speedy recovery! Thanks for all that stopped by as we had many great conversations and sold a bunch of gear.
I have a ton of takeaways of how to improve the booth for next year. For those that were frustrated with the crowds and being able to see everything – we heard you loud and clear and I’ll figure out how to massively improve.

Online orders are being fulfilled and we have nearly caught up on the queue. A few items went fully out of stock and we have shipping availability notes on the product pages that have some lead time.
The team will be out in Las Vegas for summer camp – Black Hat USA, Bsides LV, and DEF CON. This means orders from 8/1 to 8/11 will go out around 8/12.
DEF CON 23 is right around the corner as well. I have a bias towards offense topics and hardware hacking topics, but here are the talks I’d want to learn more about:
- Drive It Like You Hacked It: New Attacks and Tools to Wirelessly Steal Cars
- Don’t Whisper my Chips: Sidechannel and Glitching for Fun and Profit
- Build a free cellular traffic capture tool with a vxworks based femoto
- How to Hack a Tesla Model S
- HamSammich – long distance proxying over radio
- LTE Recon and Tracking with RTLSDR
- How to Train Your RFID Hacking Tools
- ThunderStrike 2: Sith Strike
- Key-Logger, Video, Mouse — How To Turn Your KVM Into a Raging Key-logging Monster
- Remote Exploitation of an Unaltered Passenger Vehicle
- Hacking Electric Skateboards: Vehicle Research For Mortals
- NSA Playset: JTAG Implants
- RFIDiggity: Pentester Guide to Hacking HF/NFC and UHF RFID
Black Hat USA is coming up quickly and I’m excited to hear about all the latest research the community has been working on. I have a bias towards offense topics and hardware hacking topics, but here are the talks I’d want to learn more about:
- Emanate Like a Boss: Generalized Covert Data Exfiltration with Funtenna
- Take a Hacker to Work Day – How Federal Prosecutors Use the CFAA
- Understanding and Managing Entropy Usage
- Adventures in Femtoland: 350 Yuan for Invaluable Fun
- Red vs Blue: Modern Active Directory Attacks Detection and Protection
- Remote Exploitation of an Unaltered Passenger Vehicle
- Stranger Danger! What is the Risk from 3rd Party Libraries?
- Certifi-gate: Front-Door Access to Pwning Millions of Androids
- Breaking Access Controls with BLEKey
- Panel: How the Wassenaar Arrangements Export Control of Intrusion Software Affects the Security Industry
- Forging the USB Armory an Open Source Secure Flash-Drive-Sized Computer
- ZigBee Exploited the Good the Bad and the Ugly
- Broadcasting Your Attack: Security Testing DAB Radio in Cars
- ThunderStrike 2: Sith Strike
